How to Implement Restricted Shell
According to man page of /usr/lib/rsh, the actions of rsh are identical to those of sh, except that the following are disallowed:
- changing directory
- setting the value of $PATH
- specifying path or command names containing /
- redirecting output (> and >>)
According to man page of /bin/rksh, the actions of rksh are identical to those of ksh, except that the following are disallowed:
- changing directory
- setting the value of SHELL, ENV, or PATH
- specifying path or command names containing /
- redirecting output (>, >|, <>, and >>)
- changing group
Let's start to see how restrictive it can be:
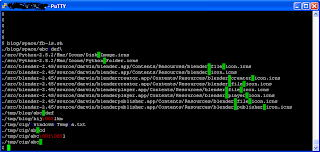
#As you can see, your search PATH does not exist and therefore you have no access to any of the binaries. Also, you really cannot run anything with absolute or relative path. The only commands you can run are the builtin commands likePATH=/some/dir/do/not/exist /bin/rksh #ls /bin/rksh: ls: not found #cd / /bin/rksh: cd: restricted #/usr/bin/ls /bin/rksh: /usr/bin/ls: restricted #echo $PATH /some/dir/do/not/exist #../../../usr/bin/ls /bin/rksh: ../../../usr/bin/ls: restricted #pwd / #echo abc abc
echo and pwd. That's far too restrictive. In order to really limit the users to run only a subset of commands, we create a /rbin directory and copy (or hard link) binaries that are absolutely required. In this demo, I only provide ls, vi, more and grep.
#mkdir /rbin #for i in ls vi more grep do ln /usr/bin/$i /rbin/. done #PATH=/rbin /bin/rksh #ls /var/adm acct log messages.2 sm.bin utmpx aculog messages messages.3 spellhist vold.log exacct messages.0 pool streams wtmpx lastlog messages.1 sa sulog #more /etc/release Solaris 10 1/06 s10x_u1wos_19a X86 Copyright 2005 Sun Microsystems, Inc. All Rights Reserved. Use is subject to license terms. Assembled 07 December 2005 #grep Solaris /etc/release Solaris 10 1/06 s10x_u1wos_19a X86 #date /bin/rksh: date: not found
I am sure you feel pretty convinced that you are really in control of what your users can and cannot run. Now all you have to do is to set their login shell and ensure /etc/profile set the corresponding PATH to the restricted directory (/rbin).